Top 5 Security and Data Breaches in 2020
In 2020, due to the pandemic, almost everything shifted from offline to online. This change opened a door for more complex cyber-attacks. No matter the business industry or company size, application security solutions became a top priority for business owners. The most extensive data breaches happened in 2020. Cybercriminals targeted several Fortune 500 companies. They could access and sell account credentials, sensitive data, confidential information and financial records of these businesses, causing severe damages and substantial monetary losses.
In this article, we will talk about the biggest data breaches in 2020, including the type of attacks, losses, and takeaways. Follow along for more information.
What Are Security and Data Breaches?

Any event that results in illegal or unapproved access to computer data, networks, devices or applications is called a security breach. The intruder can access every piece of information without authorization by hacking the security mechanism. It is important to emphasize the distinction between a security breach and a data breach. A security breach is a security incident where hackers break into your website, network, device, application, or computer but do not steal any sensitive data. A data breach is when the cyber attacker is getting away with information.
You must know that confidential information has tremendous value as they are often sold on the dark web. Sensitive data such as credit card numbers and names are often used to identify theft and fraud. Security breaches often cause companies huge monetary losses. On average, for major corporations, the damages are almost 4 million dollars.
The Most Common Security and Data Breaches
There are numerous types of security breaches or data breaches that hackers use to affect major or minor organizations. Still, at the same time, they can be used by malicious actors to break into individual’s computers and devices. Let’s explore together the most common types of cyber threats and attacks.
Security Breaches

Based on how the cyber-attack is designed to get access to the system, the most used techniques are:
- Exploit attacks that target the system’s vulnerability, such as an outdated operating system. Systems that have not been updated and use an old version of the software are open to exploits.
- Weak passwords that can be easily cracked or guessed. Passwords such as “password”, “12345”, or “pa$$word” are no longer secure.
- Malware attacks are used to gain access to corporate networks. The easiest way to start a malware attack is by sending phishing emails. Through these emails, malicious software starts spreading throughout the network.
- Drive-by downloads use compromised or spoofed websites to spread viruses or malware.
- Social engineering is also used to gain access to a network. Bad actors can call an employee, claiming to be a part of the company’s IT staff and ask for the password to help them fix the computer.
Data Breaches

For a data breach to happen, it is often necessary for a cybersecurity incident to occur and result in a security breach. It would be best if you remembered that no company is immune to data breaches, and you will read all about that in the next section of this article.
Now, let’s see what the most common data breaches that companies have to avoid are:
- Stolen information – this can happen through a cyber attack or even through human error. For example, Apple experienced an unfortunate event when an employee left a new iPhone prototype to lay around. In just a few hours, the unreleased phone’s specifications and hardware were all over the internet. This can also happen with personal details, user records, credit card details, internal records, security codes, etc.
- A ransomware attack happens when you receive a message stating that your digital devices have been hacked, and the person that did it will turn it over to you only if you pay a fee. If you don’t pay, they can choose to release the sensitive information on your device, such as credit card records, medical records, etc. The fee may vary from hundreds to thousands of dollars. To avoid ransomware attacks, companies hire risk management solution companies.
- Recording keystrokes can happen when cybercriminals or external actors insert or email you a malware called keyloggers. The keylogger records everything you are typing into your computer. Everything you typed is sent back to the hackers. They will use the received information to access sensitive data. This cyber-attack can happen at your company or to your personal device. The keyloggers will record everything users are typing: email addresses, social security numbers, login credentials, personal details, user accounts, employee credentials, database information, names, birth dates, etc.
- Phishing attacks come from third-party hackers. They create websites that look authentic to the original one. This form of attacks does not target only major companies but universities as well. Any online website or application can be a victim of website mirroring. Even PayPal and O365 applications (Sharepoint and OneNote) have been targeted with this scheme.
- Malware and viruses are the most common form of attack, and their purpose is to wipe your computer. This can be highly harmful to companies that rely on data, such as hospitals and banks. To avoid malware and viruses, we strongly advise you to instruct your employees not to click on any link they are not sure where it comes from.
Top 5 Security and Data Breaches in 2020

Analyzing or looking for patterns and trends in the breaches from previous years can help inform, educate consumers and businesses about the importance of protecting personal data. When sensitive data is compromised, not only your company but your customers are exposed to great damages. For example, more than 3.2 million customer records were exposed in the ten biggest data breaches in the first six months of 2020.
Now let’s talk about the top 5 security and data breaches in 2020. The companies that were targeted are among the largest businesses in the world. We are going to talk about Zoom, Nintendo, easyJet, Marriott Hotel Group and Twitter.
1. Zoom – Credentials Hack
The Zoom credential hack happened in the first week of April 2020, and more than 500.000 were reported to be available for purchase on the dark web. This issue concerned especially the new users of the app. The credentials were given away for free, and others were sold at a penny each. Malicious hackers leaked a wide range of sensitive information such as username, passwords, registered email addresses, host keys and personal meeting URLs. Those credentials gave the malicious actors access to the account and any contents the users might have hosted or been part of. It is very plausible that the total number of compromised users is greater than the number of accounts for sale on the dark web.
2. Nintendo – Credential Stuffing Attack
Another major data breach that happened in April 2020 had as a victim one of the gaming giants: Nintendo. More than 160.000 user accounts were put in jeopardy in a single attack. Hackers launched the credential stuffing attack and used the online accounts to buy digital products using the Nintendo network. After the cyber attack, Nintendo eliminated the log in through the Nintendo Network ID (NNID) and recommended users to use two-factor authentication methods to secure their data better. The compromised data included: account passwords, account owner names, dates of birth, country, and email address.
Credential stuffing attacks are common in the gaming and media industries. Over the years, Disney, Spotify and Netflix, all fell victim to this type of hack.
3. easyJet – Credential Theft
easyJet is a UK-based low-cost airline that has been plagued by a cyber attack, where millions of users had their data records stolen. Based on the declaration of easyJet, 9 million customer’s personal data were compromised, and 2.200 had their credit card details exposed. Because of Europe’s stringent GDPR rules, companies that violate data protection regulations are in for serious penalties. PGMBM filed a class-action lawsuit on behalf of the EasyJet victims for 23 billion dollars (18 billion pounds).
Even though easyJet has reported the matter to regulatory authorities and the Information Commissioner’s Office, the airline was too slow to inform its customers about the data breach. Some customers have found out about the cyber incident after almost four months. This is one of the biggest cybersecurity attacks and data breaches in the airline industry.
4. Marriott Hotel Group – Social Engineering Attack
Marriott was the victim of a significant data breach in March of 2020, where records of 5.2 million hotel guests were compromised. The attackers managed to obtain data from millions of users by hacking the user credentials of two Marriott Hotel Group employees. This social engineering attack highlights the importance of multi-factor authentication among the company’s employees. The hackers stole sensitive data, including names, mailing addresses, email addresses, phone numbers, gender, loyalty account information and dates of birth.
5. Twitter – Phishing Attack
On the 15th of July 2020, Twitter underwent a security breach called a phone spear-phishing attack. The threat actors used employee credentials to access the internal system. After gaining access to the platform, they targeted 130 high-profile Twitter accounts such as Barack Obama, Bill Gates, Elon Musk, and more. The hackers tweeted from 45 accounts, accessed the direct messaging inbox of 36 accounts and downloaded Twitter data of 7 accounts.
The tweet below was shared on several high-profile accounts, and it reached more than 350 million people. The tweet resulted in the recovery of 121.000 dollars (in bitcoin) in stolen “donations” within hours.
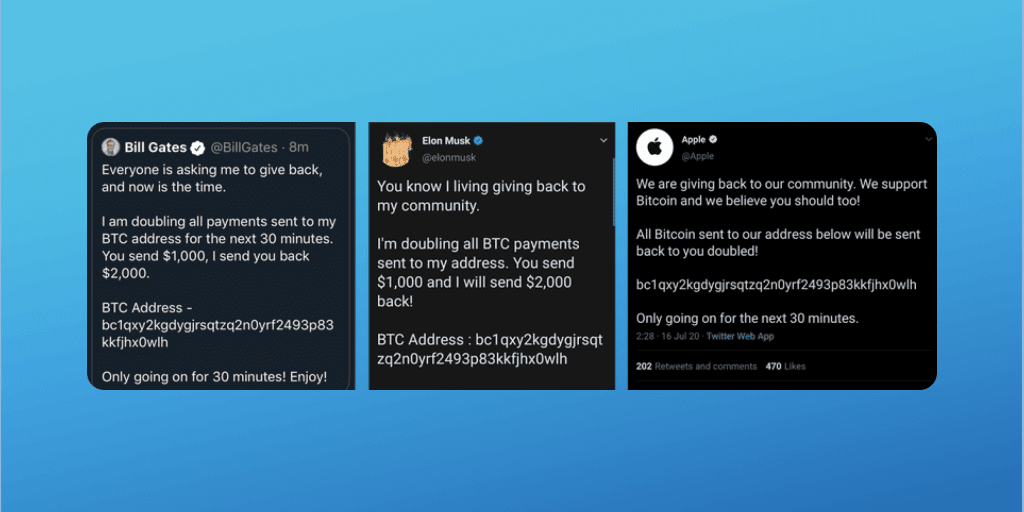
Twitter addressed this attack later on and described it as social engineering. The cybercriminals used psychological manipulation to trick and mislead employees and exploit human vulnerabilities to gain access to the platform and steal a wide range of sensitive information.
Other 5 Security and Data Breaches of 2020 Worth Mentioning
On our list of data and security breaches of 2020, we would like to include other 5 instances where millions of users were exposed to data leaks.
- Mailfire, an email marketing company, experienced a massive data breach that resulted in the exposure of sensitive data of over 70 adult dating and eCommerce websites that were using Mailfire software. The malicious actor accessed the software through Mailfire’s unsecured Elasticsearch server. The hacker collected around 320 million data records of over 100 thousand users. The exposed data consisted of notification contents, personal information (real names, gender, age, date of birth), private messages, authentication tokens and links, IP addresses, profile pictures and biography descriptions.
- Broadvoice is a telecommunications vendor that left the database of the Voice over IP (VoIP) accessible on the internet. Security experts discovered the unprotected database of more than 350 million records. The database included information about: full caller names, caller identification numbers, phone numbers, voicemail records, locations and dates of birth.
- Magellan Health, Fortune 500 company, experienced a ransomware attack in April 2020, where 365.000 patient sensitive information was compromised. The hacker started the cyber attack by installing malware to get employee login credentials. In the second step of the health service attack, the hacker posed as a Magellan Health client in a phishing attack to gain access to the company’s server, and the third step was to implement the ransomware. The hacker gained access to employees login credentials, ID numbers and patient’s details such as Social Security numbers, taxpayer ID numbers.
- Keepnet Labs is a security firm from the UK. They suffered a data breach that affected 5 billion records. The cybersecurity firm collects and stores publicly known data breach information into their Elasticsearch database. During scheduled maintenance of their Elasticsearch database, the engineer disabled the firewall for 10 minutes to speed up the process. During this time, BinaryEdge (an internet indexing service) indexed the data and made it publicly available. The compromised data contained information about the reported data breaches that happened between 2012 and 2019. The leaked information was: source of the breach, year of the breach, breached email address, breached password or hash, and the format of the breached password.
- MGM Resorts reported a massive data breach that exposed records of over 10 million hotel guests, including some high-profile persons such as Justin Bieber, Jack Dorsey (CEO Twitter), and prominent government officials. The leaked database containing information about 10.6 million people was uploaded on a hacker forum for free. The total number of stolen records reached 142 million. The information about the hotel guests that got published by the hacker included: customer names, home addresses, phone numbers, email addresses and dates of birth.
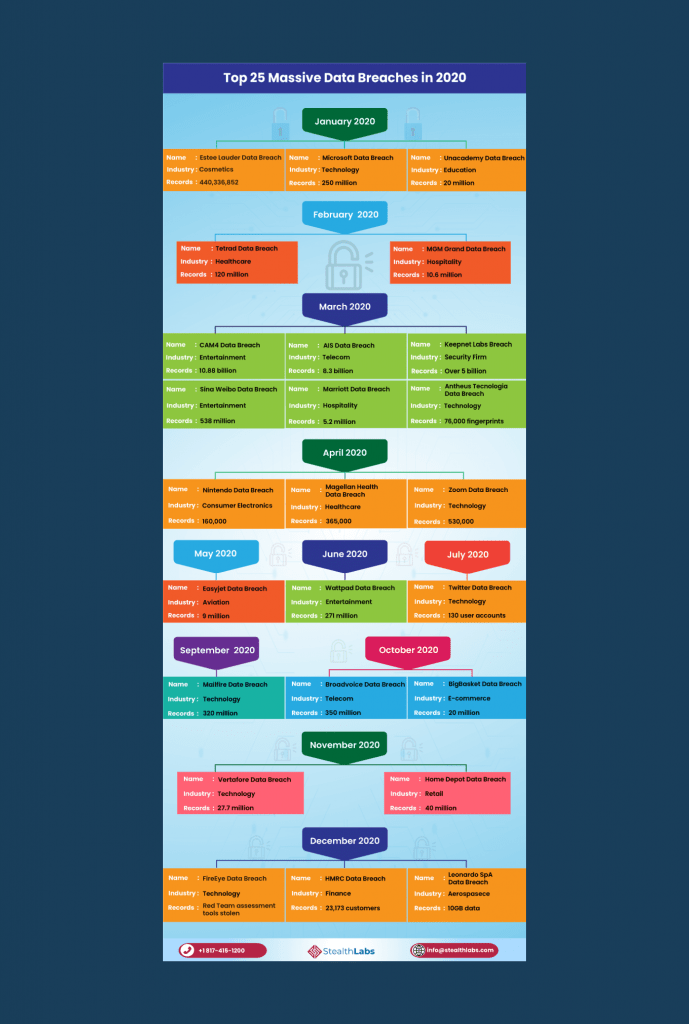
StealthLabs created the following infographic with the 25 most overwhelming data breaches that made the headlines in 2020:
Our Advice – How to Avoid Any Breaches

When we look at the most significant data breaches from 2020, most of them happened because of negligence. Application security solutions are the smartest move that you can make to protect your business from any security issue that hackers can exploit.
In 2020, cybersecurity was pretty challenging for any organization, no matter its size or industry. Unfortunately, many companies are not prepared to handle a significant cybersecurity incident. According to the Ponemon Institute, 77% of organizations do not have a CSIRP (Cybersecurity Incident Response Plan).
To prevent data and security breaches, we have some recommendations you can implement:
- Use encryption to prevent a leaky database and any sensitive data loss.
- Enforce unified data protection policies across all servers, networks and endpoints.
- Use a vulnerability and compliance management tool to identify gaps, weaknesses and security misconfigurations. Your security team can better understand the risks and create a plan to minimize the vulnerabilities.
- Conduct regular security audits and create documents on information security policies.
- Train and educate all employees and staff, no matter their role in the company, especially on the modern phishing attacks.
- Patch and update your software as soon as options are available.
- Upgrade your devices and drivers.
- Use a VPN service and antivirus protection.
- Use multi-factor authentication.
We think that this “explosion” in cybersecurity incidents happened because the remote working environment was implemented very suddenly in 2020. Many companies were not prepared for this switch and did not have the remote networking capabilities shielded. Because of this shift, many businesses left unsecured gaps that hackers could exploit for their financial gain or disrupt the operations’ flow.
The priority now is to eliminate any vulnerability and to implement stronger security protocols.
We can help you with application security solutions, fix any gap in your endpoints, identify and eliminate vulnerabilities. Contact us today, and let’s make sure you have a strong security protocol in place, your business is secure, and you are protected against any unauthorized party accessing your systems.
Frequently Asked Questions
Very easy if they find vulnerabilities to exploit. Usually, it takes almost four steps to access your systems.
Depends on what the hacker wants to obtain. From what we saw, they prefer techniques such as phishing, social engineering and credential stuffing.
The most frequent motivation is financial (86%).
No. Security researchers (good hackers) want to make the internet a safer place, but some malicious people abuse their skills.